The client faced significant security challenges during the modernization of their legacy Point of Sale (POS) system. Built with Java, Hibernate, and an Oracle database backend, the legacy system exhibited inherent security vulnerabilities, making it difficult to manage and protect sensitive data.
Continue Reading
Solution: Implementing security measures for cloud-based modernization
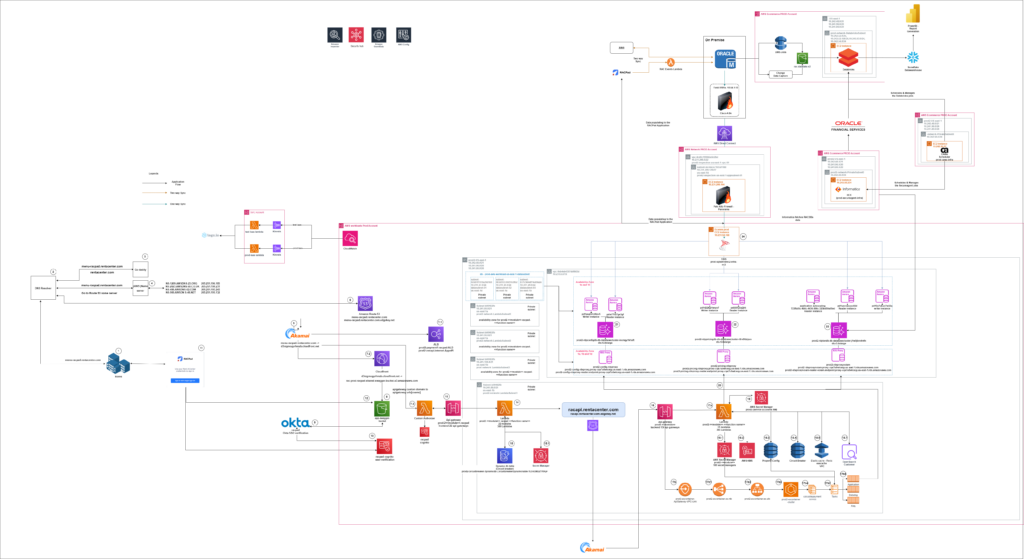
- Data Encryption: We ensured end-to-end encryption of data during migration and at rest by utilizing AWS Key Management Service (KMS) to securely manage encryption keys, protecting sensitive information from unauthorized access.
- Access Controls: We implemented strict access controls using AWS IAM roles and policies, enforcing the principle of least privilege and restricting access to authorized personnel only.
- Secure Data Migration: We employed AWS Database Migration Service (DMS) to ensure a secure data transfer process. Tasks were managed at the module level for precise synchronization, incorporating Oracle-side transformations and staging tables to enhance data protection.
- Monitoring and Compliance: We utilized AWS CloudTrail and AWS CloudWatch for comprehensive monitoring and logging, facilitating real-time detection of suspicious activities and ensuring compliance with industry security standards and regulations.
Benefits:87% secure migration process and 89% enhanced system resilience
- Achieved an 87% secure migration, ensuring data integrity and protection through secure data transfer and precise task management.
- Realized a 67% reduction in vulnerabilities with a redesigned data model and microservices architecture, significantly enhancing system resilience.
- Improved monitoring and compliance by 95%, enabling real-time threat detection and ensuring adherence to security standards and regulations.
- Enhanced system resilience by 89% with the new architecture, bolstering security and allowing comprehensive monitoring tools to detect security incidents in real time and maintain compliance with industry standards.
Are you facing similar challenges with your legacy systems?
Through the modernization of their legacy POS system, we successfully enhanced our client’s data security and streamlined their operations, enabling them to serve their customers more effectively while adhering to industry regulations. Our targeted security measures not only protected sensitive information but also created a resilient infrastructure for future growth.
Let us help you modernize your operations and secure your data. Contact us today to learn how our solutions can optimize your business and protect your sensitive information.